How Do Security Tokens Work | It acts like an electronic key to access something. In the u.s., these are is regulated by the security and and there's still the question of how to count telegram's $1.7 billion private token sale. This guide addresses how to prepare a security token offering and the issues you need to consider to get started on your token offering journey. Security token offering meaning and regulation. But what is a security token in the first place?
The microsoft identity platform implements security tokens as json web tokens (jwts) that contain claims. This is where token authentication comes into effect. Although security tokens and tokenized securities may have a similar appearance and terminology, issuing security tokens has nothing to do with tokenized securities. If there are so many new companies, how the internal. An issuer (like the reit fund manager or the pizza shop owner) issues a security token which represents an ownership claim in a company.
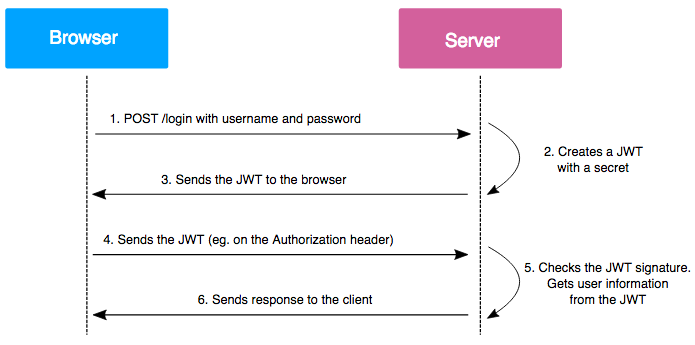
How security tokens are used in crypto field? He examines the technology behind them and why their. A security token is a peripheral device used to gain access to an electronically restricted resource. Security token exchanges and security tokens are the fastest growing concepts in the trading economy but before diving deep into exchanges first we need here's a quick overview of the different types of security tokens: Security tokens are cryptographic tokens that represent a security as defined by the local regulations. What are the other uses of security tokens? Examples include a wireless keycard opening a locked door. This guide addresses how to prepare a security token offering and the issues you need to consider to get started on your token offering journey. However, just because tokens attract new kinds of investors does not mean you can create an offering with complete disregard towards regulation. How do security token offerings work? How can ordinary investors like you participate in the sto market? What is a security token: The advantages of tokens are security, protection, verification and regulatory compliance, but you lose the object of value when you lose the token.
The advantages of tokens are security, protection, verification and regulatory compliance, but you lose the object of value when you lose the token. Differences between sto, ipo, and ico. If a token passes the howey test, it is a security token. In the u.s., these are is regulated by the security and and there's still the question of how to count telegram's $1.7 billion private token sale. This table provides an overview.

Sto regulation in the world. In a traditional sense, securities can represent an. The howey test firstly, let's briefly define security tokens. An issuer (like the reit fund manager or the pizza shop owner) issues a security token which represents an ownership claim in a company. Tokenized securities allow for businesses to lock in funds without locking investors in because the tokens are tradable on a secondary market. Security tokens can well be the next big megatrend of the blockchain revolution. Differences between sto, ipo, and ico. The token is used in addition to or in place of a password. Depending on the how the token is set up, it may be eligible for trading in global markets. A security token can be as big as a key fob or as small as a microchip. The advantages of tokens are security, protection, verification and regulatory compliance, but you lose the object of value when you lose the token. You should consider whether you understand how cfds work and whether you can afford to take the high risk of losing your money. Json web tokens and claims.
But more recently, the crypto economy has entered a bear. How do security token offerings work? This is where token authentication comes into effect. The microsoft identity platform implements security tokens as json web tokens (jwts) that contain claims. How do security tokens work?

Security tokens are highly similar to traditional securities, which include stocks, bonds and options, however with a strong technological upgrade additionally, the blockchain industry has been plagued by regulatory uncertainty, something that security token exchanges will have to work with as well. However, just because tokens attract new kinds of investors does not mean you can create an offering with complete disregard towards regulation. There are security token services (sts) that can issue you with a security token and confirm your identity. A security token transactions differs from traditional crypto transactions in many ways. Security tokens can well be the next big megatrend of the blockchain revolution. Solarwinds remote monitoring and management. A security token can be as big as a key fob or as small as a microchip. How do these work on the internet? It acts like an electronic key to access something. The howey test firstly, let's briefly define security tokens. How do security tokens work? A security token is a peripheral device used to gain access to an electronically restricted resource. This is where token authentication comes into effect.
How Do Security Tokens Work: Like securities, security tokens are tradeable assets whose value lies in something external.
EmoticonEmoticon